TUF Client
RSTUF makes it easy to host and manage TUF metadata for a content repository.
In order to effectively protect client implementations, artifacts from the content repository along with metadata served by RSTUF must be downloaded or updated. These artifacts can then be interpreted in a TUF-compliant way.
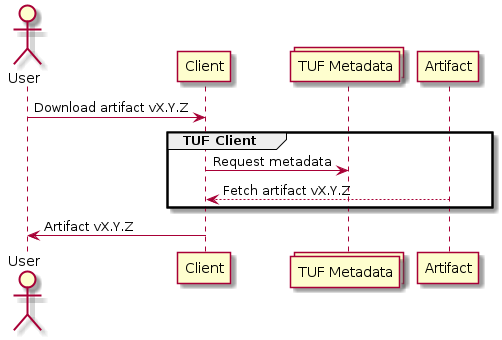
RSTUF itself does not provide client-side tools, but there are several TUF libraries available.
TUF client implementation
There are a number of options for new or existing client applications.
New client
To establish a new client implementation, consider using python-tuf’s ngclient. It can download and validate metadata and artifacts in a fully specification-compliant way. Moreover, RSTUF is built with python-tuf and guaranteed to be compatible with ngclient. See client example application to get started.
Existing client
For existing client implementations ready for download and update artifacts, metadata download and validation functionality can be integrated using a TUF library available in a variety of application languages.
Language |
Project |
|---|---|
Python |
|
JavaScript |
|
Go |
|
Rust |
Note
Not all TUF libraries support all features of the TUF specification. If the TUF library required is not compatible with RSTUF or does not exist yet, it may be necessary to file a bug on the relevant repository, or reach out to the TUF community.
Bootstrap trust
To bootstrap an initial trust relationship with the metadata repository, a client application needs to be initialized with root metadata. This can be provided out-of-band, as part of the client application, or via Trust-on-first-use (TOFU). TOFU is demonstrated in the python-tuf client example application.
Once initial trust is established, any subsequent trust changes can be adopted by the client in-band, including root key rotation.